[ad_1]
GameOver(Lay) Vulnerability: New Privilege Escalation Vulnerabilities Influence Ubuntu Programs
Safety researchers S. Tzadik and S. Tamari at Wiz have lately found two new privilege escalation vulnerabilities within the standard Filesystem OverlayFS, codenamed “GameOver(Lay)”. These vulnerabilities have an effect on a major variety of Ubuntu customers worldwide, accounting for about 40% of all Ubuntu customers. On this article, we’ll present detailed details about these vulnerabilities and information you thru the steps to test in case your Ubuntu system is weak.
Extreme Linux Vulnerability Impacts Ubuntu Programs
The primary vulnerability, recognized as CVE-2023-2640, is assessed as high-severity with a CVSS v3 rating of seven.8. It impacts Ubuntu Kernels above model 5.15.0. This vulnerability permits underprivileged customers to set privileged prolonged attributes on mounted information or file programs, granting them elevated privileges over the system.
The second vulnerability, often known as CVE-2023-32629, is categorized as medium-severity with a CVSS v3 rating of 5.4. It impacts all Linux Kernels with model 5.4.0. This vulnerability exploits a race situation within the kernel’s reminiscence administration subsystem when accessing the Digital Reminiscence Space (VMA), resulting in arbitrary code execution.
These vulnerabilities will be traced again to modifications launched by Ubuntu to its model of the OverlayFS module in 2018. These modifications have been met with objections from the Linux Kernel Challenge, significantly relating to the setting of prolonged attributes that outline consumer permissions. Though Linux launched a repair for this vulnerability in 2020, the modifications weren’t included into Ubuntu’s modification of the module.
Ami Luttwak, Wiz’s Chief Technical Officer and co-founder, acknowledged, “Delicate modifications within the Linux kernel launched by Ubuntu a few years in the past have unexpected implications. We discovered two privilege escalation vulnerabilities brought on by these modifications, and who is aware of what number of different vulnerabilities are nonetheless lurking within the shadows of the Linux kernel spaghetti?”
In response to Mike Parkin, Senior Technical Engineer at Vulcan Cyber, “Thankfully, whereas these vulnerabilities could be simple to use, they require native consumer entry, which ought to restrict the assault floor. Ubuntu has launched patches to handle the difficulty, and deployments using the affected OverlayFS module ought to replace their kernel as quickly as attainable.”
Which Variations of Ubuntu are Weak
Wiz’s analysis signifies that the next variations of Ubuntu have been compromised:
| Launch | Kernel Model | CVE-2023-2640 | CVE-2023-32629 |
|---|---|---|---|
| Ubuntu 23.04 (Lunar Lobster) | 6.2.0 | Sure | Sure |
| Ubuntu 22.10 (Kinetic Kudu) | 5.19.0 | Sure | Sure |
| Ubuntu 22.04 LTS (Jammy Jellyfish) | 5.19.0 | Sure | Sure |
| Ubuntu 22.04 LTS (Jammy Jellyfish) | 6.2.0 | Sure | Sure |
| Ubuntu 22.04 LTS (Jammy Jellyfish) | 5.15.0 | No | No |
| Ubuntu 20.04 LTS (Focal Fossa) | 5.15.0 | No | No |
| Ubuntu 20.04 LTS (Focal Fossa) | 5.4.0 | No | Sure |
| Ubuntu 18.04 LTS (Bionic Beaver) | 5.4.0 | No | Sure |
Test if Your System is Weak or Not?
To find out in case your Ubuntu model is weak, observe these steps:
- Open the terminal and execute the next command:
cat /and so forth/os-release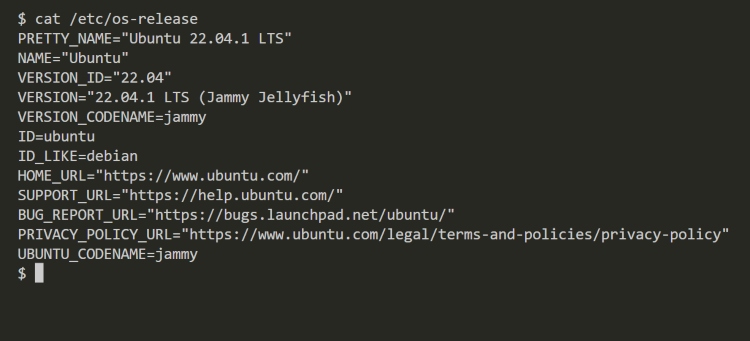
- Test for the kernel model quantity by working the next command:
uname -r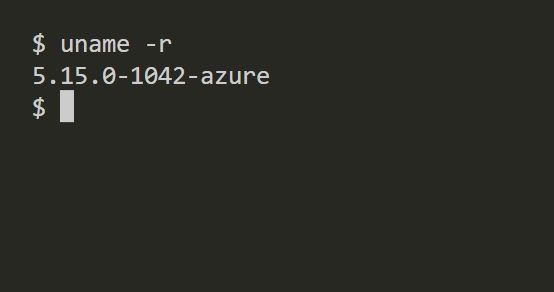
Resolve the Linux Vulnerability in Ubuntu
[ad_2]
For extra info, please refer this link
